Monday Author: Susanne Skinner
Last month I wrote a blog on the insecurity of network security. I touched on enough major points to make people slightly more conscious of internet dangers. I pinpointed the obvious failings, human and otherwise, and signed off feeling I had done a service to my readers.
 I barely scratched the surface. During my company’s annual user conference we invited a cybercrime expert to keynote who went into much more depth on the subject. It was eye opening and frightening. I didn’t know what I didn’t know.
I barely scratched the surface. During my company’s annual user conference we invited a cybercrime expert to keynote who went into much more depth on the subject. It was eye opening and frightening. I didn’t know what I didn’t know.
Cynthia James, Global Director of Business Development at Kaspersky Lab, gave us a let’s-get-real look at Cybercrime trends and their impact on people like us. Cynthia is a cybersecurity expert with one of the world’s most rigorous security certifications, the CISSP (Certified Information Systems Security Professional). She gave me permission to use her material and graciously agreed to guest post blog on The Next Phase blog. Thank you Cynthia!
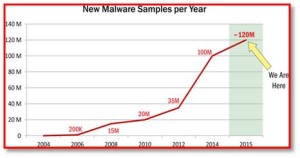
Cynthia opened her presentation with a harsh look at perception versus reality. Statistics like this make me cringe. We have a cybercrime comprehension gap – there is too much information and it’s too complicated for the average user to understand.
One of the most common misconceptions about cybercrime is that it’s never as bad as people say, and we have the government to protect and save us. The truth is, they can’t save us. With over 320 million homes users and 118 million business users there is very little the .5 million dedicated government agents can do except monitor the crimes scenes.
They compete against more than one billion entry points for malware, programs designed to harm your computer and by default; you.
Is it all Bad?
No. The darknet started in 2004 for anonymous communications in the military and to keep encryptions a secret. Darknets are small niches of the Deep Web, a term for Net-connected stuff that isn’t discoverable by major search engines. It’s called the deep web because of its size—It is massive. Here online information is password protected, hidden behind monetized sites or special-access software. By some estimates, it is 500 times larger than the Web most people search every day, yet it’s completely out of sight.
Technically, a darknet is a variation on a virtual private network (VPN) with additional measures in place to ensure that network and IP addresses of members are not discoverable. The purpose is to hide not only the communications but the fact that information is being exchanged. It’s one of the best ways to up your security and online privacy.
Members join with the expectation of sharing information and/or files with minimal risk of detection. That is relatively easy to do. They use specialized software that guarantees encryption and anonymity, and protocols or domains that even savvy web geeks won’t find.
 In countries where the right of free speech is forbidden, darknets grant everyone the power to speak without fear of censorship or persecution. They provide a refuge for the open exchange of information and ideas that would otherwise attract government or corporate censorship.
In countries where the right of free speech is forbidden, darknets grant everyone the power to speak without fear of censorship or persecution. They provide a refuge for the open exchange of information and ideas that would otherwise attract government or corporate censorship.
Cybercrime
But it also shields a vast digital underground of hackers, criminals, terrorists, and pedophiles. Weapons, human organs, assassins, drugs and counterfeit currency are but a few of the products and services available in the darkest part of this web. It is a smaller but significant internet community that trades in the most malicious crimes. When you are anonymous you can do whatever you want.
People like us access about .03% of the web using major search engines such as Google. The rest is only accessible if you are anonymous, through a deep web browser. The most famous of these is called TOR–short for The Onion Router—one of several software programs that provide a gateway to the Dark Web. It was released to the public as open-source freeware in 2004.
 TOR reroutes signals across 6,000 servers to hide a page request’s origin, making clicks on illicit material nearly impossible for law enforcement to trace. It uses secret pages with .onion suffixes—rather than .com—which are only accessible with a TOR browser.
TOR reroutes signals across 6,000 servers to hide a page request’s origin, making clicks on illicit material nearly impossible for law enforcement to trace. It uses secret pages with .onion suffixes—rather than .com—which are only accessible with a TOR browser.
Like the regular web, the dark web also hosts a network of invitation-only chatrooms and forums, hidden behind unlisted alphanumeric Web addresses that provide access to the most heinous of criminals. It is impossible to police it because people continue to develop new methods to remain invisible and off the grid. Due to the hidden nature of the sites it’s possible to find only a small number of them.
Cybersecurity
According to Cynthia, the best defense is information. The end user needs to know and care about cybercrime—and right now we don’t. Our indifference comes from common misconceptions:
 The government will save us
The government will save us- It’s not worth the effort
- I don’t know where or how to begin
- It’s not that important – I’ll do it when I have time
Until we make it a priority we remain at risk. The government cannot give us a safe online world. It is our job to create a safe infrastructure for our business, financial and social activities. Computers store and process confidential, sensitive, and private information that is part of a larger ecosystem. Weaknesses in that system open the door to malware attacks that will compromise the safety of your information.
The best way to protect yourself is to mind what you do on line. This is where you begin. Learn what you don’t know. Give yourself the awareness and tools necessary to be cyber safe.
Cybercrime is a perfect storm. Be aware of the risks, take responsibility for creating a secure computer and invest in the knowledge and programs needed to keep you and your data safe.
Statistics courtesy of Cynthia James, Kaspersky Labs
@cjonsecurity, @kaspersky
Kaseya Connect 2015 Users Conference